I've been increasingly seeing an item for Route Package Protection automatically added to my cart when I purchase things online:

If you haven't encountered Route, it's a company that offers package tracking and protection for lost, stolen, and damaged products for online merchants. Route offers plugins that integrate directly into common online store software platforms, and since Route is set up so the customer pays, it's free for the merchant. They have a mobile app that allows users to track packages, and companies can advertise within the app.
Later in the checkout flow, I have the option to remove Route Package Protection, but if I do so, it would be at my own risk:
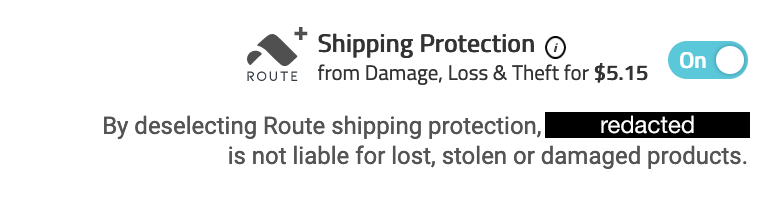
It surprised me a little to see basic shipping insurance, something that's long been built into the costs of online shopping and shipping options, has suddenly shifted to a separate, explicit upcharge for shoppers. Part of the surprise is certainly because paying for it directly as a shopper feels like I'm being charged more for something that should be a core part of online shopping. It's a little unclear what value Route provides since insurance is available through most shipping companies: perhaps, it's difficult and time consuming to make claims with shipping companies, or maybe, it's just a belief that the customer paying for Route saves the company money.
The other part of my surprise lies in this third-party service automatically getting all of the information about my purchase, whether or not my package arrives safely. In an alternate universe, Route would have designed package protection to be an insurance service that companies buy into and request assistance when something goes awry with a package. Companies might increase costs slightly to cover Route's service fees, but they might not need to due to insurance pooling. Companies would get to save time dealing with lost and stolen packages, but most importantly, this model would significantly reduce the amount of customer data shared with Route.
Unfortunately, that's not the route Route chose (sorry not sorry), and instead, Route is gathering customer purchase data across a wide swath of online vendors. Purchase history data has a direct value propostion for retailers and advertisers, especially when it's tied to your actual personal information including your address and phone number - the latter being a common key for advertising databases.
Route seems to realize this is a likely customer concern, and their Privacy and Data Security Statement (July 26, 2021) implies they won't sell your data:
When do we share it? We share personal information when needed to fulfill our legal obligations and when our vendors, business partners, and affiliates need it to perform the contracts we have with them. We provide further detail about our sharing of personal information here. We do not sell or rent any personal information from any data subjects to third party data brokers or marketing companies.
However, the extended Privacy and Cookie Statement (July 26, 2021, linked at "here") clarifies that your personal information is not actually protected in the event that the company itself is sold:
Business Sale/Purchase
If we or any of our affiliates sell or transfer all or substantially all of our assets, equity interests, or securities, or are acquired by one or more third parties as a result of an acquisition, merger, sale, reorganization, divestiture, consolidation, or liquidation, personal information may be one of the transferred assets.
Of course, this issue around personal information privacy and company acquisition isn't unique to Route, but Route is a relatively young VC-funded company, the exact sort of company I expect to be eyeing acquisition. VC firms specifically want companies to grow fast and make large exits, and one common strategy to do that is to get acquired for a lot of money. In fact, it's plausible that an entity might even want to acquire Route solely for the vast amounts of customer data it has amassed from the various online stores that use it to save a little money dealing with lost packages. Sure, it's possible that Route's investors are simply happy for it to turn into a consistent business and have no aspirations of monetizing customer data, but I'm not willing to bet that VC firms are happy to leave potential money behind.